Information Security Risk
資訊安全管理委員會組織架構
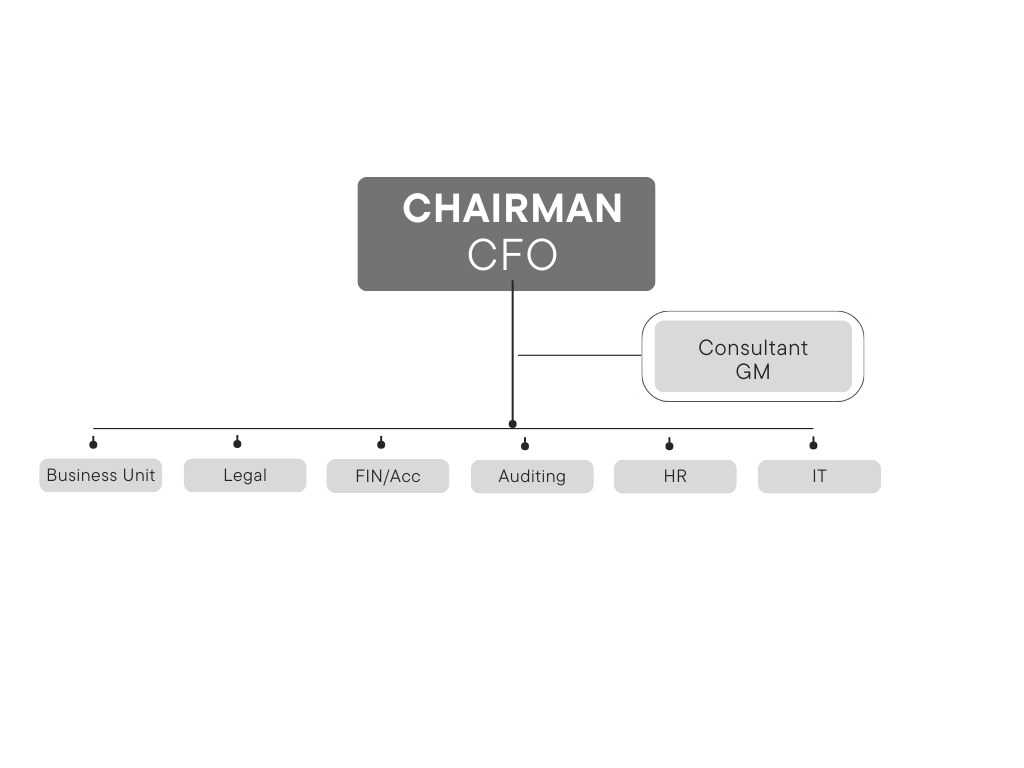
The Information Security Management Committee is established to coordinate, plan, audit, and promote unified information security management. It is responsible for strengthening information security management, ensuring the confidentiality, integrity and availability of information, the reliability of information equipment (including computer hardware, software, and peripherals) and network systems, as well as employees' awareness of information security, and ensuring that the above resources are protected from interference, destruction, intrusion, or any unfavorable acts or attempts by any factor.
Duties:
| Divison | Management Responsibilities |
|---|---|
| Information Security Management Committee | Coordination, planning, auditing and promotion of resource integration and unified information security management. |
| Business Unit | Cooperate with policy implementation |
| Legal | Provide legal support and management of litigation and non-litigation matters to ensure that interests are not jeopardized. |
| Auditing | Evaluate the implementation of the information security management system, check whether the laws and regulations have been complied with, and make recommendations. |
| Fin/Acc | Cooperate with policy implementation. |
| HR | Information security policy advocacy and education training. |
| IT | Plan and execute all information security operations. |
Information security management implementation
(B) Enhancement of employees' awareness of information security through the publication of information security advocacy journals and the implementation of email social engineering drills to raise alertness.
(C) Exposure risk monitoring, adopting non-intrusive information collection technology, through the collection of public data, network trapping mechanism and threat intelligence integration, coupled with vulnerability search engine, all the continuously collected security risk indicators will be analyzed, and thus help enterprises to monitor network risks.
(D) Computer security management
- Restrict the use of system platform administrator privileges to reduce the chance of computer poisoning, intentional or unintentional modification of system settings and arbitrary installation of illegal software, personal software derived from the legal liability and loss of the company's operations.
- Monthly computer spot checks, including anti-tampering seal checks, confirming the installation of USB device control programs, confirming the installation of file encryption software, the installation of software authorized by the company, confirming the inclusion of the company's domain, confirming the absence of private replacement or addition of components, and so on.
(F) Introducing the advanced defense module of the email filtering system, which can provide advanced defense against spearhead attacks, money transfer scams, APT attack emails, ransomware viruses, and new types of attack emails.
(G) Introducing two-factor login authentication mechanism for information system administrator accounts to strengthen the protection of privileged accounts in important systems.
(H) Build a cloud-based backup environment for SAP ERP system to enhance system security and availability.
(I) All server hosts are equipped with threat detection and response services (MDR) to immediately respond to and actively block intrusion attacks when hacker malware is launched, strengthening the resilience of important system security.
(J) Conducted system vulnerability scanning for important internal server hosts to confirm whether there are vulnerabilities in the managed devices and performed vulnerability patching operations.
(k) Reconstruct the backup system and implement cloud-based off-site backup, anti-tampering and other backup functions to ensure the security and availability of backup data.
Information security hardware and software investments
MDR threat detection and response service, system vulnerability scanning service, ERP system cloud backup environment, and backup system reconstruction, etc., the total investment in information security hardware, software, and services for this year was about NT$4,359 thousand.
ADM, SecurityScorecard, and Multi-Factor Authentication System for Privileged Accounts were introduced to the email filtering system, and the total cost of hardware, software, and services was about NT$2,169 thousand.
F5 Networks remote access equipment and email filtering system were introduced and anti-virus modules were purchased, and the related introduction and construction costs totaled about NT$1,352 thousand.